Industrial Cyber Security for Critical Infrastructure
To ensure the continuity of industrial services we use industry-leading solutions and practices to enable Industrial Control Systems (ICS) infrastructure availability, integrity, and security.
Challenges within Industrial Cyber Security
With a focus to ensure safe and secure continuity of industrial processes in today’s world, Industrial Cyber Security has become paramount. Industrial Control Systems (ICS) infrastructure availability, integrity and security is a high priority for operating companies. Operating companies are being challenged in many ways to maintain an environment free of cyber threat and protected from vulnerabilities. These challenges are being driven by an evolution in ICS environment designs that bridge connectivity between business and ICS, the introduction of new technologies into ICS, and the sharing of maintenance and support responsibilities between IT and OT. Industrial cyber security is necessary for critical infrastructure and the storage and exchange of information.

Service Description
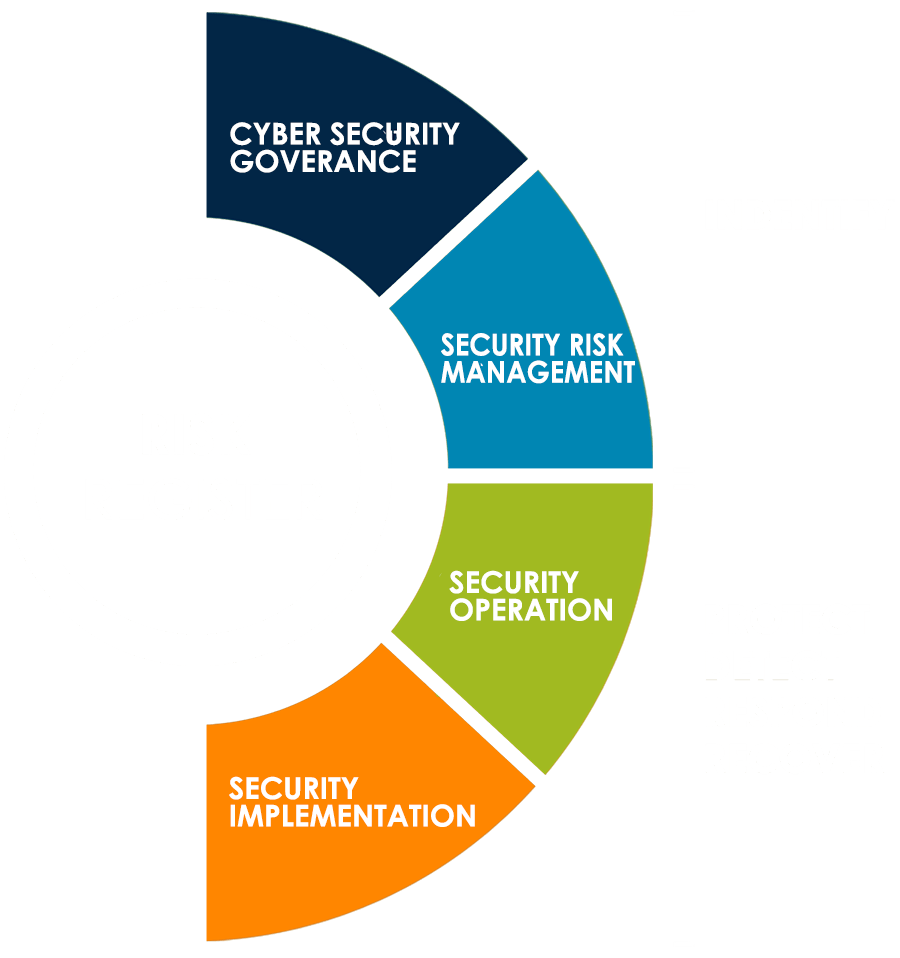
Our Industrial Cyber Security services brings our expertise and knowledge to you through four services delivery models, including industrial network security, operational technology cyber security, and other services.
Consulting Engagements: Help you identify weaknesses in your OT people, process and technology areas that can be exploited by cyber threat actors. We help you build strategic roadmaps and plans to mature and improve your cyber security capabilities and defensibility, reducing operational risk, while maintaining safe and highly available production capabilities.
Project Implementation Services: Help you build and improve your Cyber Security capabilities leveraging our expertise. These can range from developing processes and procedures to technical solutions deployment and operationalizing the day to day activities such as monitoring, administering/managing, and responding to Cyber Security warnings or alerts from your production environment.
Staff Augmentation: Provide skills and resources to compliment your Cyber Security staff needs during times that you struggle to find resources internally or externally to fill a position on projects or day to day operations.
Managed Security Services: Our skilled staff and managed services can offer you continuity of highly trained skilled staff to manage day to day Cyber Security monitoring and management of Cyber Security infrastructure capabilities in your environment.
Client Benefit #1
You can leverage our industry experience to help you gain quick insight into your Cyber Security threats and weaknesses and prepare remediation activities that will reduce the risks associated with those threats.
Client Benefit #2
Our skilled resources and ability to source industry leading vendor solutions can help you deploy capability to improve your defensibility in an era when Cyber Security skills are difficult to acquire.
Client Benefit #3
Dexcent’s managed services can potentially monitor and manage your Cyber Security infrastructure components at a more cost effective way, while maintaining skilled resources for several clients at the same time.

Understand Cyber Security Risks and Plan for Improvements
With our Cyber Security consulting services we help our clients identify weaknesses in their OT people, process and technology environments that can be exploited by cyber threat actors, and help them build strategic roadmaps and plans to mature and improve their Cyber Security capabilities and defensibility, reducing operational risk, while maintaining safe and highly available production capabilities.
Dexcent's Advantage: Our Cyber Security expertise for industrial controls environments leverage many years of IT and OT experience across many industries and help our clients to realistically assess cyber threats to their environments. We help our clients understand the real cyber threat risks and impact to their business, by assessing and advising on the real impact on people’s safety and health, environmental impacts, and the estimated cost of production interruption and reputational damage that can be experienced by successful cyber incidents.

Assessments
Assessing Industrial Control Systems infrastructure Cyber Security risk. Assessments could include:
-High level Cyber Threat impact reviews.
-In-depth OT network Architecture and Design reviews.
-System Security Configuration Reviews.
-System and network Vulnerability Assessments.
-Cyber Security Control Compliance readiness Assessments (help you prepare for formal compliance audits).
DEXCENT'S ADVANTAGE
Our assessments and planning activities help our clients better understand real potential cyber threat impacts to their specific environment and enable them to plan for remediation and implementing operational resiliency (detect, protect, response) capabilities custom build to safeguard environment against cyber attacks.
Testing
Testing controls for Cyber weaknesses or vulnerabilities. Testing could include:
-Network or System Penetration Testing.
-Control practices effectiveness testing (People, Process, Technology).
DEXCENT'S ADVANTAGE
Our testing services is very OT production and safety focused and help our client validate weaknesses in people, process and technology controls in your environment to defend against cyber attacks. The outcomes of our testing services help our clients clearly understand priorities and risks based on your actual production environment and build remediation plans that is commensurate with actual risk to the business.


Forensics
Cyber Security investigations of incidents with required chain of custody retention of evidence for judicial processing if and when required.
DEXCENT'S ADVANTAGE
Our technical Forensics experts helps clients analyze Cyber Security incidents (such as root cause and any damage incurred, and can identify threats still in progress or resident in environment) while professionally preserve evidence that can be leveraged in litigation or legal recourse.
Technology Solution Evaluations
Evaluation of various technology solutions with recommendations for a set of requirements to meet your Cyber Security controls. This would include paper based evaluations of various solutions and could include leading proof of concepts (POC) evaluation of recommended solutions before final purchase and implementation decisions are made.
DEXCENT'S ADVANTAGE
Our industry expertise across many clients in various industries and our technology partner relationships allow us to evaluate right fit technology solutions for or client's Cyber Security defensibility and operational requirements. Our clients leverage our expertise to quickly evaluate various solutions, working closely with their own teams and with industry solution providers to help identify advantages and disadvantages for various solutions and we make recommendations for our clients to quickly assess and select the solution of choice to be acquired and implemented.
This reduce the burden on own resources to study alternatives and bring external experiences into effect to enhance the process of selection. Dexcent is an independent party that has no vendor product allegiance and thus can be trusted as an independent and trusted advisor. Although Dexcent has partnerships with a few technology vendors, these are for fulfillment purposes to gain best advantage in supplying a solution and providing support during and after implementation. We are not incented to sell these products and assess each solution evaluation on merits of the client's requirements and best fit scenarios.


Awareness
Cyber Security Threat Awareness training that meet your organization needs, could include:
-Development of a complete awareness training program or pieces of such a program.
-Targeted training for Executives, staff (all or group/roll based).
-Regular Cyber Security threat awareness updates addressing new or highly probable threats concerning your industry and cyber infrastructure.
DEXCENT'S ADVANTAGE
We leverage our experience across many industries to assess and advise on your Cyber Security Awareness Training Program's needs and good industry Awareness training delivery platforms. Dexcent’s experience can help you build the best Awareness Training delivery solution for your environment.
Planning / Strategy / Roadmaps
Our Cyber Security professionals helping you with developing your Cyber Security Strategy, Remediation Plans, and Implementation Roadmaps that aligns with your Industrial Automation strategy and plans. Strategy and Roadmaps are typically multi-year plans that captures the outcome of Cyber Security controls assessments or new controls required by major infrastructure or business changes in your environments. These plans and roadmaps are typically adjusted annually or even sooner when major unplanned infrastructure changes occurs or your business or industry Cyber threat landscape changes.
DEXCENT'S ADVANTAGE
Dexcent’s experience with ICS automation and OT Cyber Security requirements, bring a rich suite of real industrial control systems hands-on experience to the table which provide solid support for our advise and guidance to you in planning and strategizing around OT Cyber Security capability improvements.
We also understand the needs of the enterprise and integration with corporate and IT Cyber Security practices and IT services management practices (such as incident management, change management, availability management, vulnerability and patch management, and governance and risk reporting metrics) to support and align with enterprise Cyber Security strategy and plans.


KNOWLEDGE. EXPERTISE. EXPERIENCE
With our Cyber Security project implementation services we help you with Solution Design and Implementation, Securing infrastructure through security configuration reviews and associated remediation activities, remediation of controls gaps identified in compliance reviews or audits, developing and implementing Cyber Security practices (policies, processes, standards, guidelines, and procedures), and the implementation of Cyber Security Incident Response Management capabilities.
Dexcent's Advantage: With our Cyber Security project implementation services we bring experienced technical implementation resources to you to compliment your project management planning, design and implementation teams. Our resources understand Industrial Control Systems and OT technology and integration requirements and are obsessed with Process Automation and Cyber Security Risk management requirements unique to OT environments.

Solution Architecture / Design / Implementation
Professional services that help you preparing solution Architecture and Design documentation and specifications. Skilled professionals that help with planning and the implementing of solutions from documented design materials, assist with solution customization, and perform testing and training if required.
DEXCENT'S ADVANTAGE
Dexcent’s Cyber Security architects and designers of Cyber Security solutions, can add value to your team by bringing good practices and experience into the team to help define and develop clear understanding of solution requirements and implementation activities. Common solutioning areas include: network segmentation and access management, asset and configuration management, vulnerability and patch management, and incident management (monitoring and response).
Security Infrastructure – Configuration Reviews and Changes
Performing system configuration reviews against defined system standards or hardening practices and implement required changes.
DEXCENT'S ADVANTAGE
Our team of experts have hands-on experience with most vendor products in the OT environment which range from network infrastructure products (switches, routers, firewalls, wired and wireless access and radio networks) and ICS vendors platforms. They can do network architecture and design, and device configuration reviews. They can also help you with remediation activities to implement changes to meet your minimum security requirements driven by policies and standards.


Developing of Cyber Security Controls Practices
Providing professional expertise to develop required control practices (Policy, Processes, Standards, Guidelines, Procedures) to meet your requirements
DEXCENT'S ADVANTAGE
Dexcent’s Cyber Security experts have experience in IT and OT environments and are familiar with good practise and international standards and Cyber Security Frameworks. We can assist you to develop or enhance your Cyber Security practices (Policies, Processes, Standards, Guidelines, and Procedures) that will address any compliance requirements or meet your Cyber Security goals and maturity posture expectations. Not only can they help with developing these practices, they can also help you implement the controls and monitor for effective enforcement of the controls. This could help you with being prepared for providing controls evidence if you are to be audited for compliance, and ensuring that your management reporting is substantiated with effective and enforced controls.
Controls Gap Remediation Services
Skilled professionals to assist with implementation of Cyber Security controls remediation activities or tasks.
DEXCENT'S ADVANTAGE
Our experienced cyber security team members are familiar with most Cyber Security control frameworks and can help your teams with the activities required to perform remediation activities to close the findings gaps identified in formal assessments or audits reports.


Incident Response Services (on-call / on-site)
Professional emergency services to help you during a Cyber Security incident when your incident response team need additional external help to contain and resolve.
DEXCENT'S ADVANTAGE
During a serious Cyber Security incident you need reliable and trusted partners that know your OT environment to assist your internal teams with effective and timely response. As a trusted service provider Dexcent could coordinate your external emergency professional services by working with your own team members (IT/OT/Process Control Engineers), your OT systems vendors (SCADA/DCS/network vendors), our trusted emergency services partners, or partners you have chosen based on the circumstances to provide the emergency or complex investigation, analyses and response activities. Urgent response via the phone or on site support are desirable under such circumstances and speed of response is of the essence. We would welcome the opportunity to plan for delivery and execute such service with you, by bringing experienced senior management resources, our delivery teams, and any other partners to the table to custom build the plan and service to meet your requirements.

Obtaining and maintaining Cyber Security skilled resources are an ongoing industry challenge
Globally the demand for Cyber Security resources are a challenge across all geographies and industries. More so for experienced resources in your local locations, that are familiar with OT environments, and understanding the unique requirements of industrial control processes. This leads to a scramble to find resources and maintaining them onboard for projects and ongoing operational support activities.
Dexcent's Advantage: Dexcent historically has provided services for Industrial Controls Automation and work with many SCADA/DCS and controls system suppliers in Canada. We have many connections across industry and access to qualified resources and maintaining a staff compliment that supports our client’s demands.

Infrastructure Build and Roll-out Projects
When you have long term projects that need experienced staff to project manage or execute implementation activities and tasks under your management leadership and oversight, we can assist with finding and supplying staff on a contract basis over a period of time.
DEXCENT'S ADVANTAGE
Dexcent has several resources allocated on long term assignment on large transformation or new roll-out projects across several prominent Industrial Controls automation clients in Canada.
Administrative or Operations Staff:
When you have ongoing day-to-day need for Cyber Security administrative tasks or operational monitoring and services management activities and found yourselves in a bind with skilled staff to perform these activities, Dexcent may be able to help sourcing skills for an interim period to meet your short term needs
DEXCENT'S ADVANTAGE
Dexcent has several resources allocated on long term assignment on technical support roles across several prominent Industrial Controls automation clients in Canada.

Think | Automate | Secure

Providing OT/ICS leaders with the insight needed to make effective decisions with complex business processes in a secure, worry-free way.
THINK
We think about your data, the technologies you have, and the stories they tell of what is happening, what can happen and what has happened. We create insight so you can make effective data driven decisions.
AUTOMATE
We automate complex OT/ICS business processes by understanding the operational risks, management of change realities and compliance subtleties that are important to you for achieving better outcomes in keeping people, assets and the environment safe.
SECURE
We secure your OT/ICS environment by identifying cyber risks early, continuously measuring your security posture for weaknesses and threats while working with you to improve your cyber resiliency year after year.
We're Obsessed with Process Automation
We admit it, we’re obsessed. We’re obsessed with creating insight, improving complex business processes and ensuring your
cyber resiliency year after year.





